By Tyler Durden
By Tyler Durden
Anyone who got a COVID-19 test at Walgreens might have had personal data left online, including their name, date of birth, phone number, address, and email. In some cases, the results of the COVID tests were left on the open web for anyone to see, according to a new report by Recode.
Security vulnerabilities on the Walgreens COVID website were first discovered by Alejandro Ruiz, a consultant with Interstitial Technology PBC. He said: “Any company that made such basic errors in an app that handles health care data does not take security seriously.”
Recode told Walgreens of Ruiz’s findings, which two other security experts verified. Recode granted Walgreens time to fix the vulnerabilities before publishing the story, but Walgreens didn’t comply.
It was found that people’s sensitive data could be exposed to ad tracking websites. The platform’s vulnerabilities are an example of how a megacorporation promoted itself as a “vital partner in testing” that rushed out a testing registration platform that didn’t take privacy and security seriously.
When asked, Walgreens did not specify how long security vulnerabilities were present on its platform. There’s reason to believe the vulnerabilities began as early as July 2020.
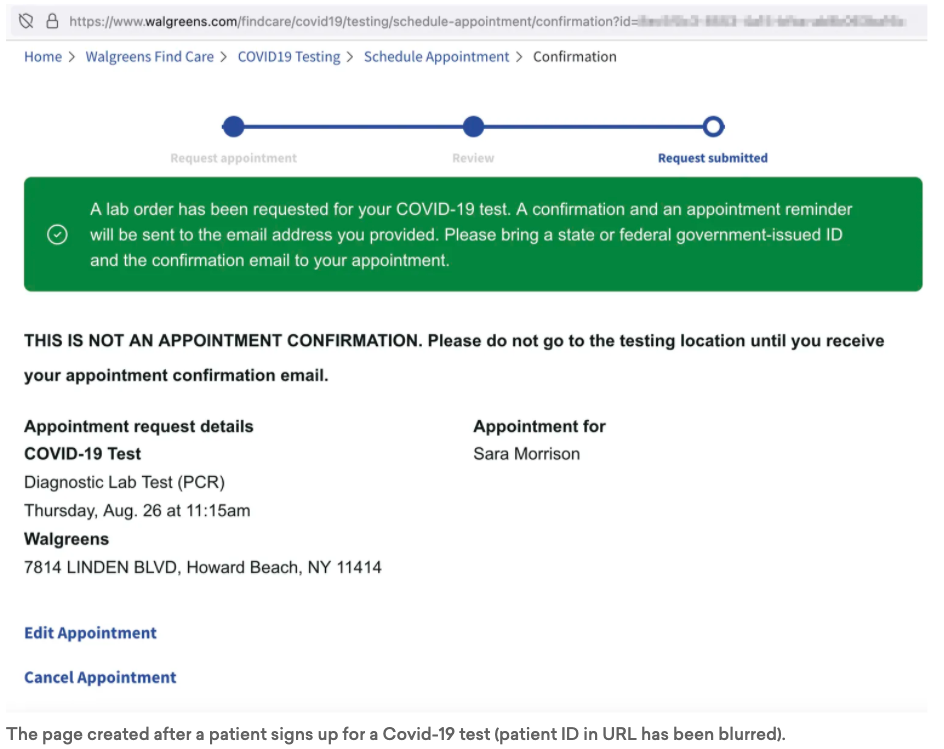
The problems are in Walgreens’ Covid-19 test appointment registration system, which anyone who wants to get a test from Walgreens must use (unless they purchase an over-the-counter test). After the patient fills out and submits the form, a unique 32-digit ID number is assigned to them and an appointment request page is created, which has the unique ID in the URL.
Anyone who has a link to that page can see the information on it; there’s no need to authenticate that they are the patient or log in to an account. The page remains active for at least six months, if not more. -Recode
“The technical process that Walgreens deployed to protect people’s sensitive information was nearly nonexistent,” Zach Edwards, privacy researcher and founder of the analytics firm Victory Medium, said.
Security experts told Recode that active IDs could be guessed, or a hacker could create an algorithm that would rapidly generate URLs in the hope of uncovering active pages.
“Security by obscurity is an awful model for health records,” Sean O’Brien, the founder of Yale’s Privacy Lab, said.
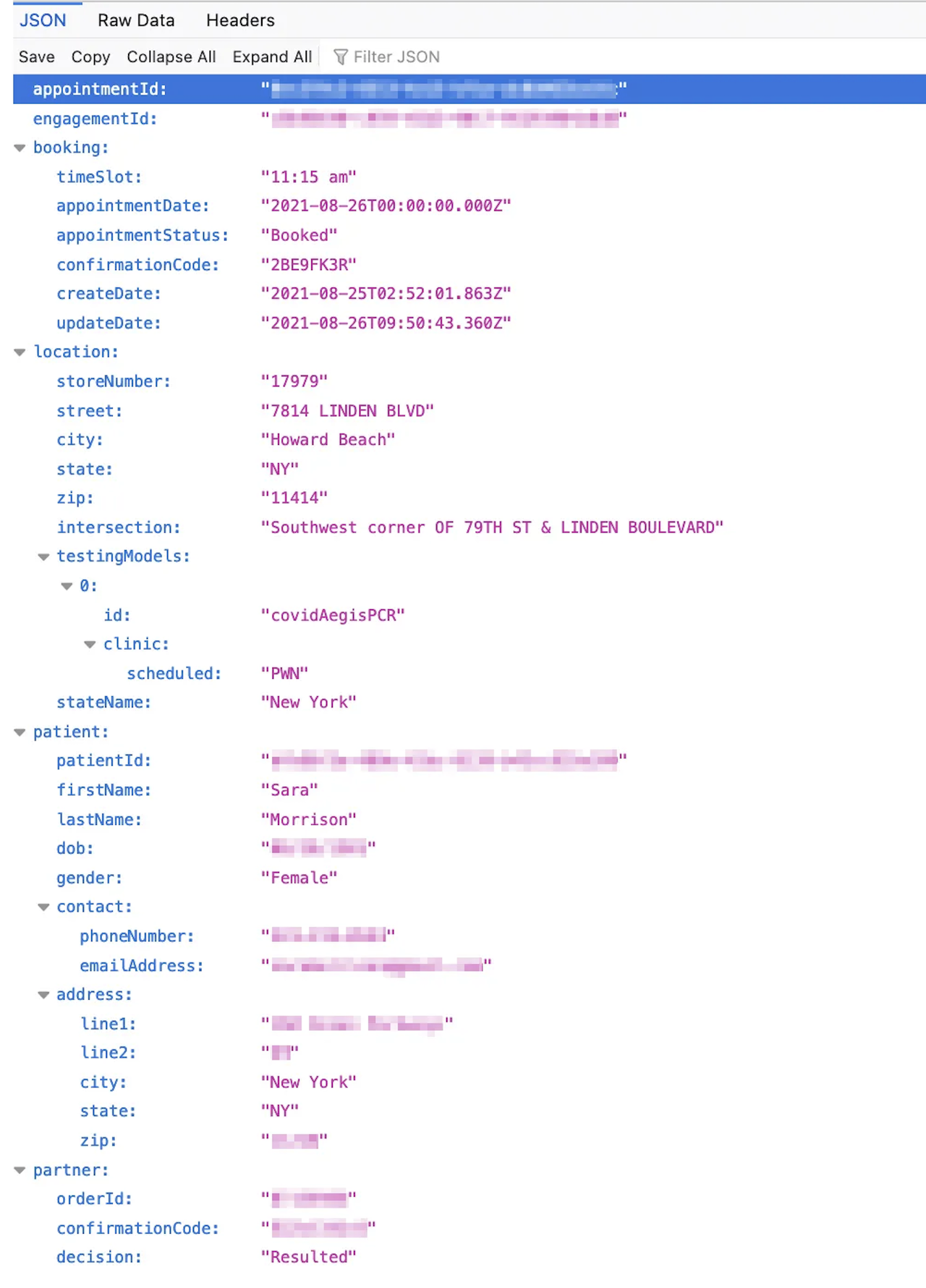
The extent of the data left open on the testing registration platform includes full name, date of birth, phone number, email address, mailing address, and gender identity. Recode said with a few clicks in a browser’s developer tools panel, anyone with access to an active page can find this sensitive information.
Ruiz and the other security experts told Recode they were alarmed by Walgreens’ trackers on its confirmation pages. They said Adobe, Akami, Dotomi, Facebook, Google, InMoment, and Monetate were some of the tracking websites that might have collected patient IDs that could then be used to find URLs of the appointment pages then access patient information.
“Just the sheer number of third-party trackers attached to the appointment system is a problem, before you consider the sloppy setup,” O’Brien said.
“This is either a purposeful ad tech data flow, which would be truly disappointing, or a colossal mistake that has been putting a huge portion of Walgreens customers at risk of data supply chain breaches,” Edwards said.
Walgreens told Recode that it was a “top priority” to protect its patients’ personal information:
“We continually evaluate our technology solutions in order to provide safe, secure, and accessible digital services to our customers and patients,” the pharmacy said.
Recode presented Walgreens with a deadline to fix the security vulnerabilities on the testing registration platform but didn’t fix the issue in time:
Again, Walgreens did not fix the issues before the extended deadline Recode provided to the company, nor would it tell Recode if it planned to do so. It did not address Recode’s questions about the ad trackers except to say that its use of cookies is explained in its privacy policy. However, tracking through cookies was not the issue Recode and Ruiz identified to Walgreens, and the company didn’t comment further when this was explained to it. -Recode.
“This is a clear-cut example [of this type of vulnerability], but with Covid data and tons of personally identifiable information,” Edwards said. “I’m shocked they are refuting this clear breach.”
Millions of people got COVID tests through Walgreens, and it remains unclear how many were exposed to this careless security flaw.
“It’s just another example of a large company that prioritizes its profits over our privacy,” Ruiz said.
Source: ZeroHedge
Image: Pixabay
Become a Patron!
Or support us at SubscribeStar
Donate cryptocurrency HERE
Subscribe to Activist Post for truth, peace, and freedom news. Follow us on Telegram, HIVE, Flote, Minds, MeWe, Twitter, Gab, Ruqqus, and What Really Happened.
Provide, Protect and Profit from what’s coming! Get a free issue of Counter Markets today.
Walgreens’ COVID Test Website Might Have Exposed Patient Data, Security Experts Say