In the latest release of ‘THE TWITTER FILES,’ journalist Matt Taibbi details how Twitter acted as a ‘subsidiary’ of the FBI.
As a reminder, parts 1-3 of the series covered respectively, Twitter’s decision to interfere in the 2020 election by censoring the Hunter Biden laptop story, how the company created secret blacklists, and how they justified removing former President Donald Trump despite internally agreeing that he didn’t break any rules (parts one, two and three).
Take it away, Matt:
Continued:
3. Twitter’s contact with the FBI was constant and pervasive, as if it were a subsidiary.
4. Between January 2020 and November 2022, there were over 150 emails between the FBI and former Twitter Trust and Safety chief Yoel Roth.
5. Some are mundane, like San Francisco agent Elvis Chan wishing Roth a Happy New Year along with a reminder to attend “our quarterly call next week.” Others are requests for information into Twitter users related to active investigations.
6. But a surprisingly high number are requests by the FBI for Twitter to take action on election misinformation, even involving joke tweets from low-follower accounts.
7. The FBI’s social media-focused task force, known as FTIF, created in the wake of the 2016 election, swelled to 80 agents and corresponded with Twitter to identify alleged foreign influence and election tampering of all kinds.
8. Federal intelligence and law enforcement reach into Twitter included the Department of Homeland Security, which partnered with security contractors and think tanks to pressure Twitter to moderate content.
9. It’s no secret the government analyzes bulk data for all sorts of purposes, everything from tracking terror suspects to making economic forecasts.
10. The #TwitterFiles show something new: agencies like the FBI and DHS regularly sending social media content to Twitter through multiple entry points, pre-flagged for moderation.
11. What stands out is the sheer quantity of reports from the government. Some are aggregated from public hotlines:
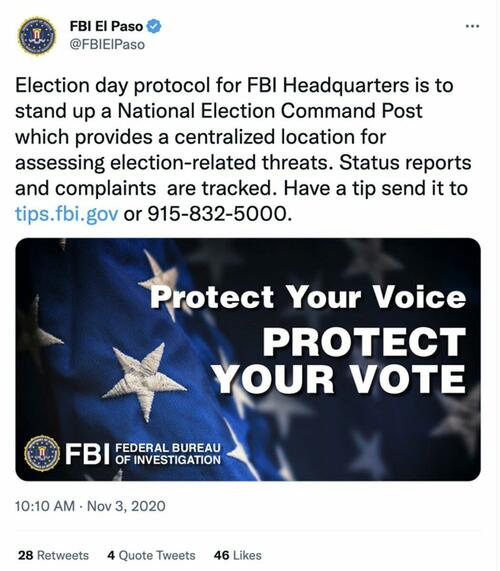
12. An unanswered question: do agencies like FBI and DHS do in-house flagging work themselves, or farm it out? “You have to prove to me that inside the fucking government you can do any kind of massive data or AI search,” says one former intelligence officer.
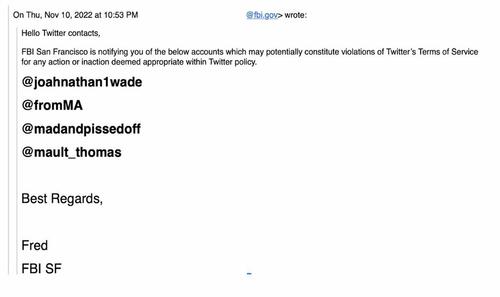
13. “HELLO TWITTER CONTACTS”: The master-canine quality of the FBI’s relationship to Twitter comes through in this November 2022 email, in which “FBI San Francisco is notifying you” it wants action on four accounts:
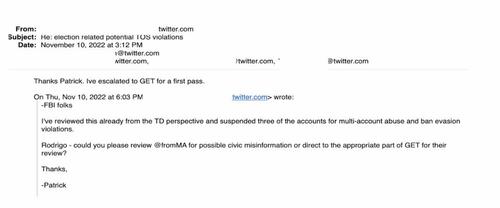
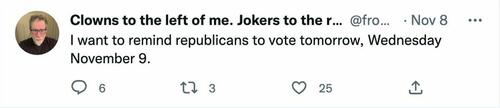
14. Twitter personnel in that case went on to look for reasons to suspend all four accounts, including @fromMA, whose tweets are almost all jokes (see sample below), including his “civic misinformation” of Nov. 8:

15. Just to show the FBI can be hyper-intrusive in both directions, they also asked Twitter to review a blue-leaning account for a different joke, except here it was even more obvious that @ClaireFosterPHD, who kids a lot, was kidding:

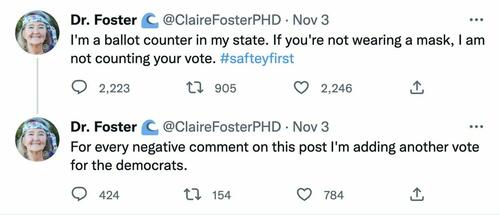
16. “Anyone who cannot discern obvious satire from reality has no place making decisions for others or working for the feds,” said @ClaireFosterPHD, when told about the flagging.
17. Of the six accounts mentioned in the previous two emails, all but two – @ClaireFosterPHD and @fromMA – were suspended.
18. In an internal email from November 5, 2022, the FBI’s National Election Command Post, which compiles and sends on complaints, sent the SF field office a long list of accounts that “may warrant additional action”:

19. Agent Chan passed the list on to his “Twitter folks”:
20. Twitter then replied with its list of actions taken. Note mercy shown to actor Billy Baldwin:

21. Many of the above accounts were satirical in nature, nearly all (with the exceptions of Baldwin and @RSBNetwork) were relatively low engagement, and some were suspended, most with a generic, “Thanks, Twitter” letter:
22. When told of the FBI flagging, @lexitollah replied: “My thoughts initially include 1. Seems like prima facie 1A violation 2. Holy cow, me, an account with the reach of an amoeba 3. What else are they looking at?”
23. “I can’t believe the FBI is policing jokes on Twitter. That’s crazy,” said @Tiberius444.
24. In a letter to former Deputy General Counsel (and former top FBI lawyer) Jim Baker on Sep. 16, 2022, legal exec Stacia Cardille outlines results from her “soon to be weekly” meeting with DHS, DOJ, FBI, and the Office of the Director of National Intelligence:

25. The Twitter exec writes she explicitly asked if there were “impediments” to the sharing of classified information “with industry.” The answer? “FBI was adamant no impediments to sharing exist.”
26. This passage underscores the unique one-big-happy-family vibe between Twitter and the FBI. With what other firm would the FBI blithely agree to “no impediments” to classified information?
27. At the bottom of that letter, she lists a series of “escalations” apparently raised at the meeting, which were already “handled.”
28. About one, she writes: “Flagged a specific Tweet on Illinois use of modems to transmit election results in possible violation of the civic integrity policy (except they do use that tech in limited circumstances).”
29. Another internal letter from January, 2021 shows Twitter execs processing an FBI list of “possible violative content” tweets:
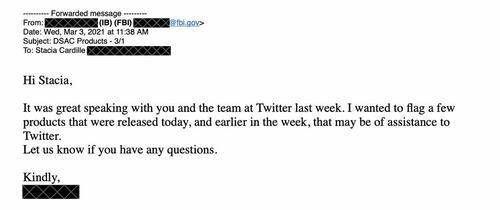
30. Here, too, most tweets contained the same, “Get out there and vote Wednesday!” trope and had low engagement. This is what the FBI spends its time on:
31. In this March, 2021 email, an FBI liaison thanks a senior Twitter exec for the chance to speak to “you and the team,” then delivers a packet of “products”:
32. The executive circulates the “products,” which are really DHS bulletins stressing the need for greater collaboration between law enforcement and “private sector partners.”
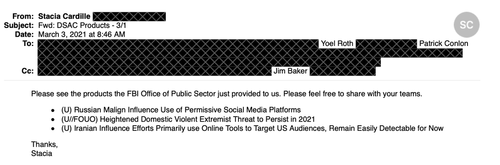
33. The ubiquity of the 2016 Russian interference story as stated pretext for building out the censorship machine can’t be overstated. It’s analogous to how 9/11 inspired the expansion of the security state.

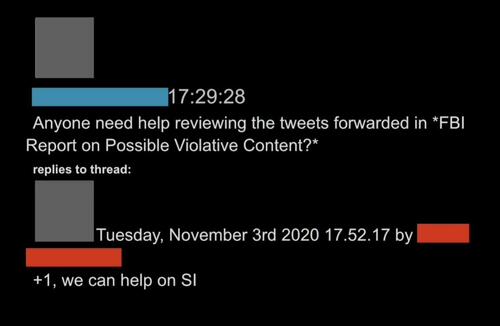
34. While the DHS in its “products” pans “permissive” social media for offering “operational advantages” to Russians, it also explains that the “Domestic Violent Extremist Threat” requires addressing “information gaps”:

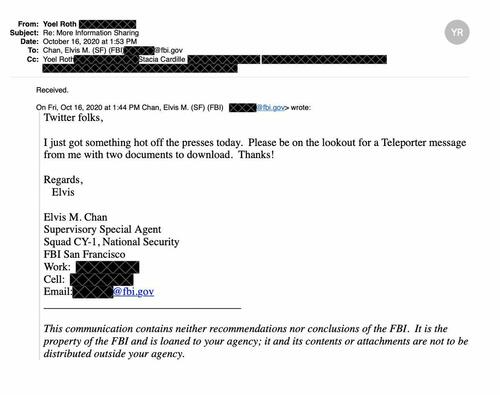
35. FBI in one case sent over so many “possible violative content” reports, Twitter personnel congratulated each other in Slack for the “monumental undertaking” of reviewing them:

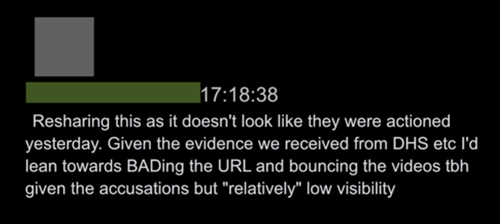
36. There were multiple points of entry into Twitter for government-flagged reports. This letter from Agent Chan to Roth references Teleporter, a platform through which Twitter could receive reports from the FBI:
37. Reports also came from different agencies. Here, an employee recommends “bouncing” content based on evidence from “DHS etc”:
38. State governments also flagged content.
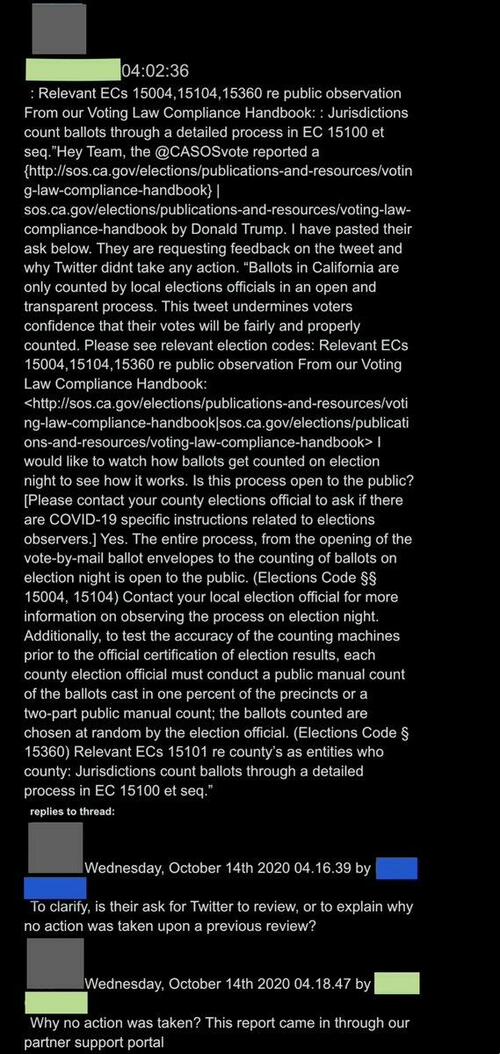
39. Twitter for instance received reports via the Partner Support Portal, an outlet created by the Center for Internet Security, a partner organization to the DHS.
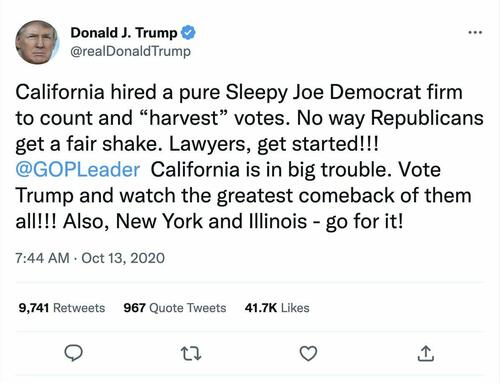
40. “WHY WAS NO ACTION TAKEN?” Below, Twitter execs – receiving an alert from California officials, by way of “our partner support portal” – debate whether to act on a Trump tweet:
41. Here, a video was reported by the Election Integrity Project (EIP) at Stanford, apparently on the strength of information from the Center for Internet Security (CIS):
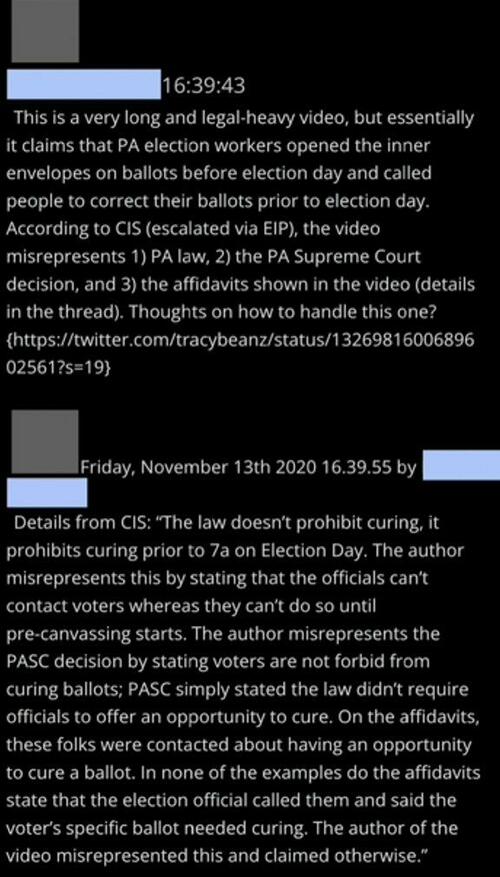
42. If that’s confusing, it’s because the CIS is a DHS contractor, describes itself as “partners” with the Cyber and Internet Security Agency (CISA) at the DHS:

43. The EIP is one of a series of government-affiliated think tanks that mass-review content, a list that also includes the Atlantic Council’s Digital Forensics Research Laboratory, and the University of Washington’s Center for Informed Policy.
44. The takeaway: what most people think of as the “deep state” is really a tangled collaboration of state agencies, private contractors, and (sometimes state-funded) NGOs. The lines become so blurred as to be meaningless.
45. Twitter Files researchers are moving into a variety of new areas now. Watch @bariweiss, @ShellenbergerMD, and this space for more, soon.
This post was originally published at Zero Hedge

 "something new"…
"something new"…